Fake Hacking Program For Mac
LAS VEGAS — Nearly a year after a patch was issued by Apple, malicious hackers can still seize control of Macs by using the Mouse Keys option built right into macOS, a security researcher said at the DEF CON 26 security conference here Sunday (Aug. 12).
- Program hacking knowledge. Week in security with Tony Anscombe. Program hacking knowledge. One of the ways in which it is distributed is through a fake Adobe Flash Player installer which is a variant of Crossrider / OSX Shlayer, essentially an adware program. Advanced Mac Cleaner then uses Siri to tell you there’s something wrong with.
- Hack like a programmer in movies and games!
Mouse Keys lets you mimic mouse movements and clicks using the number pad or the left-hand letter keys on a keyboard. Malware or an attacker can program digital representations of the feature to authorize installation of new software or to steal information from the Keychain, said Patrick Wardle, chief research officer at Digita Security.
The reason Mac isn't seen as a serious OS for hacking isn't due to the hardware. It's due to the OS itself being so closed off. Linux is a transparent OS with the capacity to control even the smallest aspects, OSX is not. Recently, a lot of fake hacking websites have popped-up on the Internet. They usually make false promises to hack the Facebook password of any account. These sites often demand people to take-up a surveys in order to complete the password hacking process.
Apple largely patched the Mouse Keys flaw in October 2017, following a demonstration by Wardle of how it could be used to steal passwords and other secrets from the Mac Keychain. But Apple left open a loophole that Wardle found by accident, and the flaw is still completely exploitable for the moment.
'I'm a huge fan of using legitimate functions of an operating system to do nefarious things,' joked Wardle.
MORE: Best Mac Antivirus Software
Controlling mouse clicks is essential to Mac security because so many of the system's defenses rely upon user alerts and authorizations. MacOS alerts you to all sorts of system changes, from installation of new software to letting applications have Keychain access to addition of new extensions.
Even if malware successfully infects a Mac — which is easier than you might think — it usually can't do much else without triggering a pop-up alert. The alert asks you to click a button labeled 'Allow' before the malware can proceed further, and if you're not expecting an alert, you shouldn't authorize the action. You're literally the last line of defense.
'On modern macOS, many exploits will be blocked unless the user authorizes an alert, even if the machine is infected,' Wardle said. 'But if you have ways to programmatically generate synthetic interactions, you can bypass a ton of these security mechanisms.'
One way for malware to get past the alert notification is to generate what Wardle called 'synthetic' mouse clicks. The malware clicks the OK button itself, often without the alert notification popping up on the screen.
For years, Wardle said, there's been a cat-and-literal-mouse game between attackers who try to find new methods to create synthetic mouse clicks and Apple, which stamps them out with each major system update.
MORE: Here's the One Gmail Setting You Should Activate Now
The most common way to generate fake mouse clicks has been through AppleScript, Apple's venerable scripting language that lets the user automate various application actions. Another way to generate synthetic mouse actions has been through the Core Graphics visual framework. Apple has blocked specific attacks based on both, but has not blocked AppleScript or Core Graphics from creating synthetic user interactions in general.
Yet Apple overlooked synthetic Mouse Keys actions as an attack vector until Wardle demonstrated his Keychain-theft approach in September 2017, right after macOS 10.13 High Sierra was released to the public.
Wardle found that fake Mouse Keys actions could be used by any process, completely defeating previous mitigations against synthetic mouse clicks. He argued that even if a pop-up alert appeared, the malware could dim the screen to zero so the user wouldn't see it before the malware clicked 'Allow.'
Despite the fact that the keyboard instead of the mouse was being used to move around the screen and click on things, Apple didn't treat the two input methods any differently, and Wardle created proof-of-concept malware that stole the Keychain contents using Mouse Keys.
MORE: Top 11 macOS Mojave Features
Apple fixed that with a supplemental update the following month. Problem solved? Not quite.
Synthetic mouse clicks are implemented by two lines of code that are nearly identical, because a mouse click is really two physical actions. First, you click the mouse button down, represented as 'true' in the Mouse Keys mimicking code. Then you let the button spring back up, which is 'false' in the code.
With its October 2017 patch, Apple blocked such code from interacting with user alerts.
But Wardle said that after that, he made a programming mistake and put two 'true' lines next to each other instead of a 'true' followed by a 'false' — and up-to-date macOS 10.13 High Sierra didn't block it. Chart program for mac.
'If you send two mouse-down events, the second translates as a mouse-up event,' Wardle said. 'I found this completely by accident, but it allows you generated synthetic events even on a fully patched system.'
So how do you prevent malware or hackers from using a synthetic Mouse Keys event to hijack your Mac? Well, right now, you can't, other than minimize the risks of infection by installing only signed applications and running Mac antivirus software.
But Apple is on top of the issue, Wardle said. AppleScript and Core Graphics-based synthetic user actions will be generically blocked in macOS 10.14 Mojave, due out next month, even if doing so might interfere with other applications.
'Unfortunately, it will also break many legitimate applications,' Wardle said.
Mac Hacking Software
Wardle's presentation slides are available on the DEF CON website.
Use the Command Prompt or Terminal to imitate hacking.Fake Hacking Screen
There are many commands that can be used in Windows Command Prompt and Apple Terminal to execute commands or query for information. The following commands, while looking impressive, will not damage your software and are not illegal.Mac Hacking Tools
- Windows users might try typing the following commands, hitting ↵ Enter after each command, in relatively quick succession to make the process seem more complex:
- color a
- This will change your Command window text from white to green with a black background. Replace the letter following 'color' with the numbers 0 - 9 or the letters A - F to change your Command Prompt font color.
- dir
- ipconfig
- tree
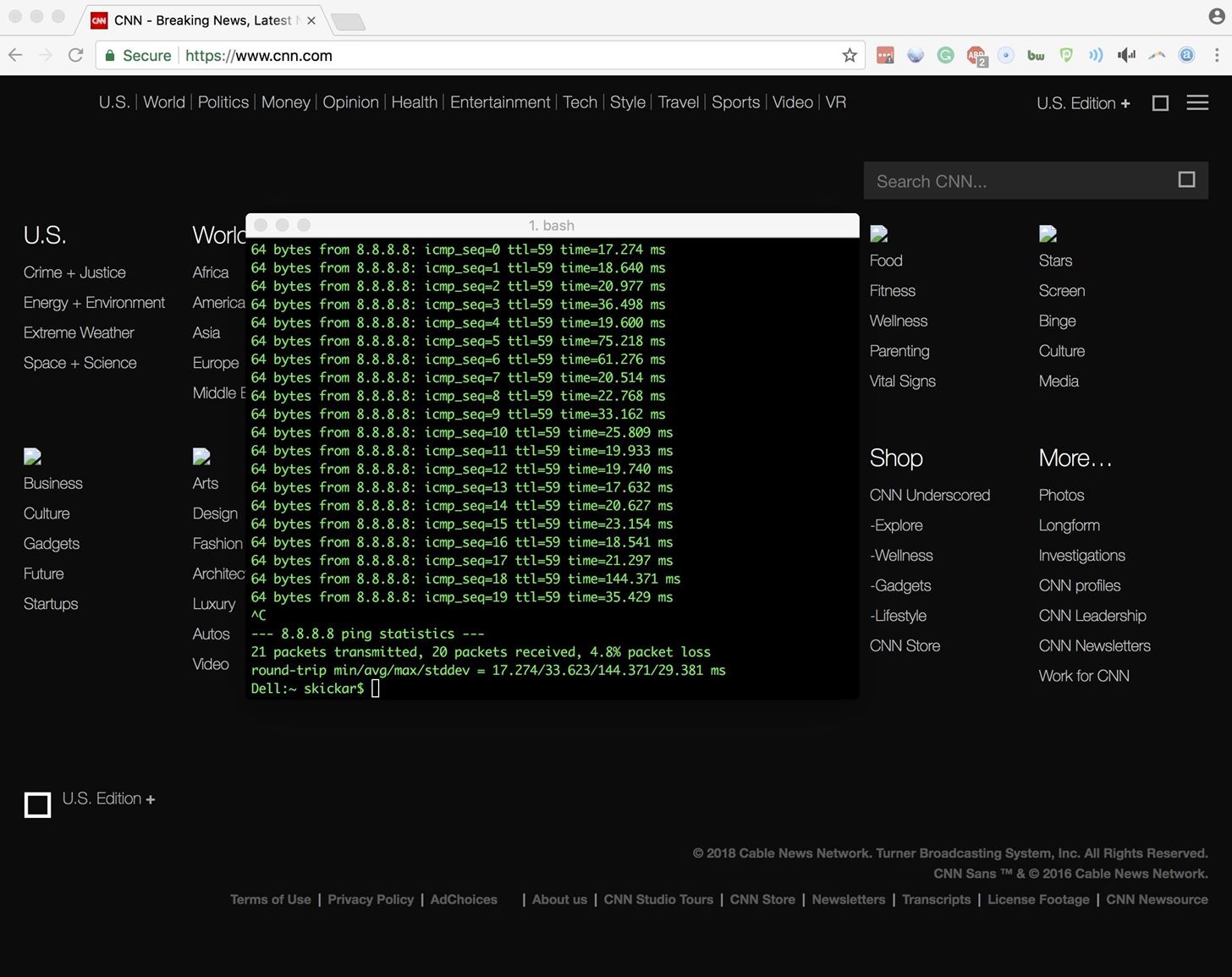
- ping google.com
- The Ping command checks if a device can communicate with another over a network (but the common person doesn't know that). Google is used as an example here, but you can use any site.
- color a
- If you own an Apple computer, you can use the following safe commands to fill your screen with what looks like professional hacking. Input the following into your Terminal window to achieve that effect:
- top
- ps -fea
- ls -ltra